
It’s game time – and while the biggest teams are gearing up for football’s biggest day, cybercriminals are busy preparing their playbook for 2025. Just like a championship game, the battle against hackers requires strategy, teamwork, and preparation.
Are you ready to tackle this year’s biggest cybersecurity threats? Here’s what the experts predict for 2025 and how your business can come out on top.
This Year’s Cybersecurity MVPs (Most Vicious Perpetrators)
1. AI-Powered Phishing Plays
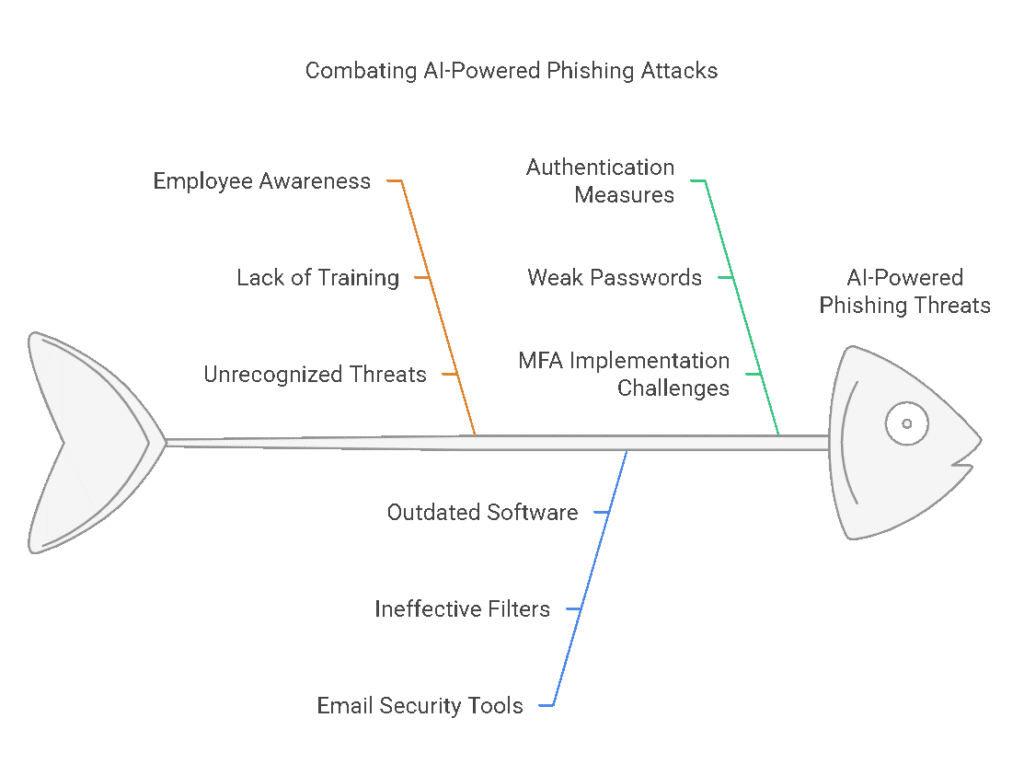
Cybercriminals are using artificial intelligence to craft highly personalized and convincing phishing e-mails that can trick even the most cautious employees. These messages look authentic, often mimicking trusted brands or colleagues.
Your Defense:
- Train employees to recognize phishing attempts.
- Implement e-mail filtering tools that detect and block suspicious messages.
- Use multifactor authentication (MFA) to protect accounts even if credentials are compromised.
2. Ransomware Blitz
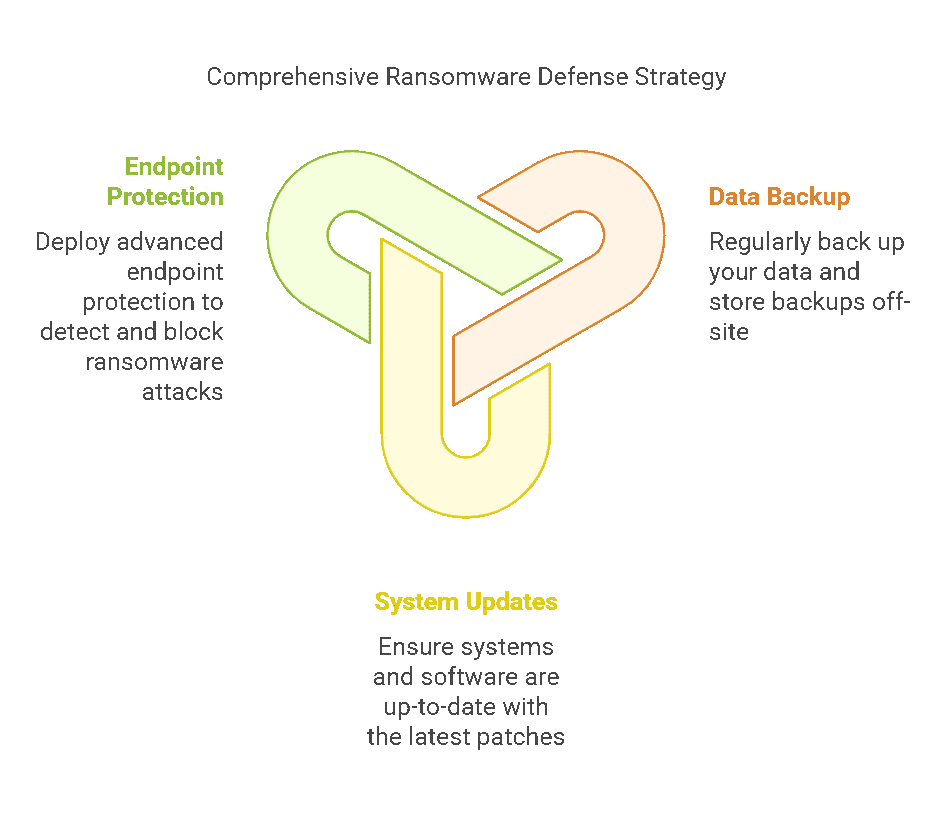
Ransomware continues to dominate as one of the biggest threats to businesses of all sizes. Hackers are not only encrypting files but also threatening to leak sensitive data if ransoms aren’t paid.
Your Defense:
- Regularly back up your data and store backups off-site.
- Ensure your systems and software are up-to-date with the latest patches.
- Deploy advanced endpoint protection to detect and block ransomware attacks.
3. Supply Chain Sneak Attacks
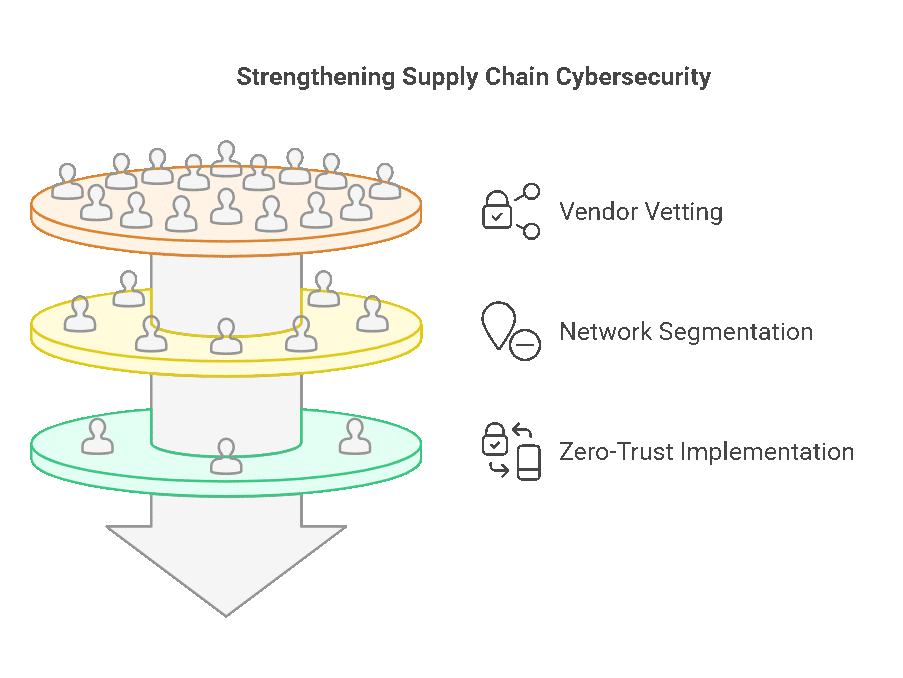
Hackers are targeting small and midsize businesses to infiltrate larger supply chains. By breaching your network, they can gain access to partners and vendors, spreading their reach.
Your Defense:
- Vet your vendors and ensure they follow strict cybersecurity practices.
- Segment your network to limit access points for attackers.
- Use zero-trust security models to verify users and devices at every step.
4. Deepfake Decoys
Deepfake technology is being weaponized to impersonate executives or colleagues, convincing employees to transfer funds or share sensitive information.
Your Defense:
- Verify any unusual requests via a second method, like a direct phone call.
- Educate your team about the potential for deepfake scams.
- Limit the sharing of sensitive information online that could be used to create convincing fakes.
5. Internet Of Things (IoT) Fumbles
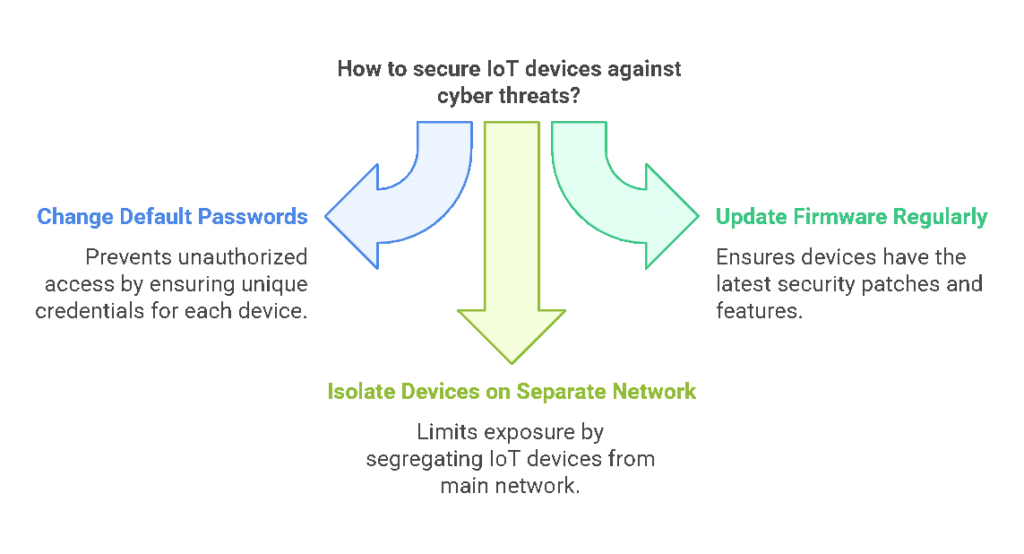
Smart devices like printers, cameras and even thermostats are often overlooked when it comes to cybersecurity. Hackers exploit these weak points to gain access to your network.
Your Defense:
- Change default passwords on all IoT devices.
- Update device firmware regularly.
- Isolate IoT devices on a separate network to limit exposure.
Your Game Plan In 2025
Winning against hackers this year requires more than just strong plays – it takes a solid game plan. Here’s how to stay ahead:
- Draft Your Team: Partner with a trusted IT provider to proactively monitor and protect your systems.
- Study The Playbook: Stay informed about emerging threats and how to counter them.
- Run Practice Drills: Regularly test your backups and conduct cybersecurity training with your employees.
Get Your Free Cybersecurity Game Plan
Ready to take your cybersecurity strategy to the next level? Schedule a FREE Network Assessment today. We’ll identify vulnerabilities, provide actionable solutions, and ensure your business is prepared to beat the hackers this year.
Click here to book your FREE Network Assessment now!
Don’t let cybercriminals win the championship. With the right team and strategy, you can protect your business and stay ahead of the game.
FAQ: Navigating Cybersecurity Threats in 2025
- How are cybercriminals using artificial intelligence (AI) to target businesses, and what can be done to defend against these attacks? Cybercriminals are leveraging AI to create highly personalized and convincing phishing emails. These messages often mimic trusted brands or colleagues, making it difficult for employees to discern them from legitimate communications. To defend against these AI-powered phishing attacks, businesses should train employees to recognize phishing attempts, implement email filtering tools to block suspicious messages, and use multifactor authentication (MFA) to protect accounts even if credentials are compromised.
- Why is ransomware still a major threat, and what strategies can businesses use to mitigate its impact? Ransomware remains a significant threat because hackers are not only encrypting files, but also threatening to leak sensitive data if ransoms are not paid. To mitigate the impact of ransomware attacks, businesses should regularly back up their data and store backups off-site, keep systems and software updated with the latest patches, and deploy advanced endpoint protection to detect and block ransomware attacks.
- What are supply chain attacks and how can businesses protect themselves from this type of threat? Supply chain attacks occur when hackers target smaller businesses to infiltrate larger supply chains. By breaching a smaller company’s network, they can gain access to their partners and vendors, thus spreading their reach. Businesses can protect themselves by carefully vetting vendors and ensuring they follow strict cybersecurity practices, segmenting their network to limit access points, and implementing a zero-trust security model to verify users and devices at every step.
- How are deepfakes being used in cyberattacks, and what are the best practices for avoiding falling victim to these scams? Deepfake technology is being weaponized to impersonate executives or colleagues, convincing employees to transfer funds or share sensitive information. To avoid falling victim to these scams, businesses should verify any unusual requests via a second method, like a direct phone call, educate their team about the potential for deepfake scams, and limit the sharing of sensitive information online that could be used to create convincing fakes.
- Why are Internet of Things (IoT) devices often a weak point in a network, and what steps should businesses take to secure them? IoT devices such as printers, cameras, and thermostats are often overlooked when it comes to cybersecurity, making them a weak point in a network. Hackers can exploit these devices to gain access to the network. To secure IoT devices, businesses should change default passwords, update device firmware regularly, and isolate IoT devices on a separate network to limit their exposure.
- What is the importance of partnering with an IT provider for cybersecurity, and how can they assist with defense strategies? Partnering with a trusted IT provider is crucial for proactive monitoring and protection of systems. IT providers can offer expertise and tools to strengthen a company’s cybersecurity posture, identify vulnerabilities, implement solutions, and stay up to date on emerging threats.
- Beyond immediate fixes, what ongoing activities are essential to maintaining strong cybersecurity defenses? Ongoing cybersecurity activities include staying informed about emerging threats and how to counter them, regularly testing data backups, and consistently conducting cybersecurity training with employees. Continuous vigilance and preparation are key to maintaining strong defenses.
- What is a Network Assessment and how can it help a business improve its cybersecurity strategy? A Network Assessment is a service that identifies vulnerabilities in a business’s network. By conducting an assessment, a business can gain actionable solutions, improve its cybersecurity strategy, and ensure its readiness to combat cyber threats. The assessment helps businesses stay ahead of potential attacks by pinpointing weaknesses and bolstering defenses.Bottom of Form