Top 10 Cybersecurity Best Practices for Small Businesses in 2025
Introduction
Picture this: You’ve spent years building your small business from the ground up. Late nights, early mornings, and countless cups of coffee have fueled your journey. Then, in an instant, it all comes crashing down because of a single phishing email that someone on your team innocently clicked.
I’ve seen it happen too many times while providing managed IT support to small businesses. The truth? Small businesses aren’t just targets for cybercriminals—they’re prime targets. And in 2025, with digital transformation accelerating faster than ever, the threats have evolved beyond what many small business owners can imagine.
Here’s the sobering reality: 43% of all online attacks now target small businesses, and a staggering 60% of small businesses that suffer a cyberattack close their doors within six months, according to a comprehensive cybersecurity guide. Those aren’t just statistics—they’re dreams shattered, livelihoods lost, and communities impacted.
But here’s the good news: you don’t need the budget of a Fortune 500 company to protect your digital assets. What you need is a strategic approach to cybersecurity that addresses modern threats while working within your constraints.
Let’s dive into the top 10 cybersecurity best practices that can shield your small business in 2025.
1. Implement Strong Password Policies and Password Management
We’ve all been guilty of using “Password123” at some point. But in 2025, weak passwords are like leaving your business’s front door wide open with a “Come on in!” sign.
Strong password policies are your first line of defense. I recommend requiring passwords that are:
- At least 12 characters long
- A mix of uppercase, lowercase, numbers, and symbols
- Not based on easily guessable information like company names or birthdays
But remembering complex passwords for dozens of accounts is practically impossible. That’s where password managers come in. Tools like LastPass, 1Password, or Bitwarden generate and store strong, unique passwords for all your accounts.
“The average employee manages access to 191 passwords. Expecting them to create and remember strong, unique passwords without a management system is setting your security up for failure,” according to cybersecurity experts at CrowdStrike.
Pro tip: Schedule quarterly password audits to identify and replace weak or compromised credentials across your organization. Most managed IT services providers include this as part of their regular security assessments.
2. Enable Multi-Factor Authentication (MFA) Everywhere
If passwords are your front door, think of MFA as adding a state-of-the-art security system. Even if someone gets your password, they still need that second verification factor—typically something you have (like your phone) or something you are (biometric data).
In 2025, enabling MFA isn’t just a good idea—it’s essential. According to Microsoft Support documentation, MFA can block over 99.9% of account compromise attacks. That’s a massive security boost for a minimal investment.
I’ve worked with small businesses in need of IT support who initially resisted MFA because they worried about convenience. But modern MFA solutions have become incredibly user-friendly. Many now offer options like:
- Push notifications to your phone
- Biometric verification (fingerprint or facial recognition)
- Hardware security keys for the highest level of protection
“MFA adoption should be non-negotiable for businesses of any size in 2025,” states a recent cybersecurity survival guide from CrowdStrike.
3. Keep All Software Updated and Patched
Outdated software is like having holes in your security fence. Each unpatched vulnerability is an invitation for attackers to waltz right in. Companies providing computer support consistently rank this as one of the most critical yet overlooked security measures.
In my experience, small businesses often delay updates because they’re worried about disruption. But automatic updates have become much more reliable, and the risk of postponing them far outweighs any temporary inconvenience.
- Set up a systematic approach to updates:
- Enable automatic updates whenever possible
- Create a monthly schedule for manually updating systems that can’t update automatically
- Maintain an inventory of all software and hardware to ensure nothing falls through the cracks
According to the FCC’s guidance for small businesses, “keeping your software updated is one of the most effective steps you can take to improve your cybersecurity posture.”
For businesses using Windows, leveraging Microsoft Support resources can help ensure all security patches are properly implemented.
4. Invest in Ongoing Security Awareness Training
The most sophisticated security systems in the world can’t protect you from an employee who unknowingly clicks on a phishing link or downloads malware.
People are often the weakest link in the security chain—not because they’re malicious, but because they haven’t been properly trained to recognize threats. This is why managed IT services NYC providers typically include security training as part of their offerings.
Effective security awareness training should:
- Be ongoing, not just a one-time event
- Include simulated phishing attempts to test awareness
- Cover the latest social engineering tactics
- Be relevant to your specific industry
I’ve seen companies reduce their phishing susceptibility by up to 75% through consistent training programs. That’s an incredible return on a relatively small investment.
“The human firewall is just as important as your technological one,” notes a comprehensive analysis of small business cybersecurity.
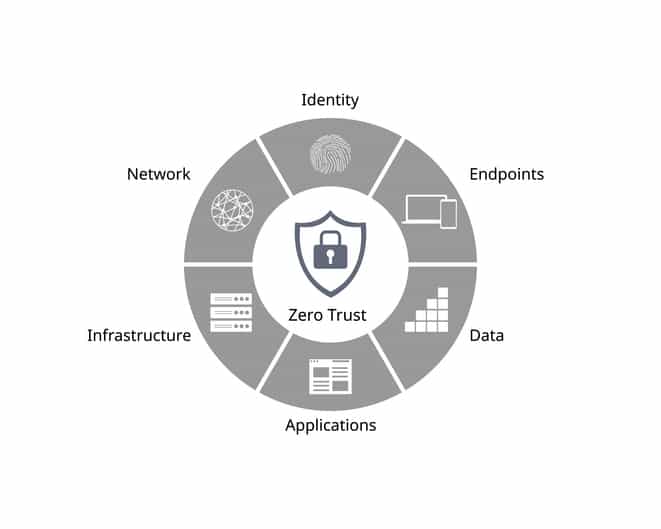
5. Implement Zero-Trust Security Models
The old castle-and-moat approach to security (where everything inside your network is trusted) is obsolete in 2025. With remote work, cloud services, and mobile devices blurring network boundaries, zero-trust is the new gold standard for cybersecurity.
Zero-trust operates on a simple principle: “Never trust, always verify.” This means:
- Every access request is fully authenticated, authorized, and encrypted
- Access is granted on a “least privilege” basis
- Systems continuously monitor and validate that users are who they claim to be
For small businesses, implementing zero-trust doesn’t have to mean a complete security overhaul. You can start with:
- Identity and access management solutions
- Network segmentation
- Continuous monitoring and verification
According to recent research, “Zero-trust adoption among small businesses increased by 33% in 2024, and is projected to reach 60% by the end of 2025.”
6. Back Up Data Regularly and Test Restorations
Imagine losing all your customer data, financial records, and intellectual property in an instant. Without proper backups, ransomware attacks can be catastrophic. Robust disaster recovery planning is no longer optional—it’s essential for business continuity.
I once worked with a small accounting firm that thought their backups were running smoothly—until they needed to restore after a ransomware attack. They discovered their backup system had silently failed months ago.
Follow the 3-2-1 backup rule:
- Keep 3 copies of your data
- Store 2 copies on different storage types
- Keep 1 copy offsite (cloud storage works well for this)
Most importantly, regularly test your restoration process. A backup is only as good as your ability to restore from it. Many managed IT services include regular disaster recovery testing to ensure your backups will work when needed.
“Among small businesses that experienced data loss in 2024, 43% had backup systems in place—but had never tested them,” according to security researchers at StrongDM.
7. Use Advanced Endpoint Protection Solutions
Traditional antivirus software isn’t enough anymore. Modern endpoint protection platforms (EPPs) use behavioral analysis, machine learning, and AI to detect and prevent sophisticated threats. This is a core component of professional IT support services in 2025.
In 2025, look for solutions that offer:
- Real-time threat detection and response
- Protection against fileless malware
- Application control capabilities
- Integrated threat intelligence
For small businesses with limited IT resources, cloud-based endpoint protection solutions offer enterprise-grade security without the need for complex infrastructure. This is an area where partnering with a managed IT services NYC provider can deliver significant value.
“The shift from signature-based antivirus to behavior-based endpoint protection has reduced successful malware infections by 62% among small business adopters,” notes a recent white paper on small business cybersecurity.
8. Secure Your Cloud Services and Applications
As more small businesses migrate to cloud services, securing these environments becomes critical. The shared responsibility model means that while cloud providers secure the infrastructure, you’re responsible for protecting your data and access.
I recommend implementing:
- Cloud access security brokers (CASBs) to monitor cloud activity
- Data loss prevention (DLP) tools to prevent sensitive information leakage
- Cloud-native security tools offered by your providers
- Regular security assessments of your cloud configurations
A common mistake I see is assuming cloud services are secure by default. In reality, misconfigurations are one of the leading causes of cloud data breaches. This is where having expert computer support or a managed IT support partner becomes invaluable.
“85% of cloud security issues can be traced back to misconfiguration rather than vulnerabilities in the cloud platforms themselves,” according to data security experts at Acrisure.
9. Develop and Regularly Test an Incident Response Plan
When (not if) a security incident occurs, how you respond makes all the difference. An incident response plan is your playbook for managing a crisis and forms a critical component of your overall disaster recovery strategy.
Your plan should include:
- Clear roles and responsibilities
- Step-by-step procedures for different types of incidents
- Communication templates for stakeholders and customers
- Documentation requirements for compliance and insurance
- Recovery and business continuity procedures
Most importantly, test your plan through tabletop exercises at least twice a year. These simulations help identify gaps before a real incident occurs.
“Small businesses with tested incident response plans recover from cyberattacks 58% faster and with 37% lower costs than those without plans,” according to FTC guidance for small businesses.
10. Partner with Managed Security Service Providers (MSSPs)
Let’s be realistic: most small businesses don’t have the resources for a full-time security team. This is where managed IT services providers and Managed Security Service Providers (MSSPs) come in.
An MSSP can provide:
- 24/7 security monitoring
- Threat detection and response
- Vulnerability management
- Compliance assistance
- Security strategy guidance
For businesses in major metropolitan areas, managed IT services NYC providers often offer specialized expertise in regional compliance requirements and threat landscapes.
I’ve seen small businesses transform their security posture by partnering with the right MSSP. It’s like having an enterprise security team at a fraction of the cost.
“By 2025, an estimated 65% of small businesses will use some form of managed security services, up from 37% in 2022,” according to industry analysis from Guardz.
Frequently Asked Questions
What are the biggest cybersecurity threats for small businesses?
The main threats facing small businesses in 2025 include ransomware, social engineering attacks (especially sophisticated phishing), data breaches, and exploitation of vulnerabilities in outdated systems. Supply chain attacks, where hackers target smaller vendors to access larger companies, have also increased by 37% since 2023.
As one cybersecurity expert put it: “Hackers view small businesses as low-hanging fruit—less protected than enterprises but with valuable data and often with connections to larger organizations.”
Why is cybersecurity important for small businesses?
The statistics tell a sobering story: 43% of online attacks target small businesses, and 60% of small businesses that suffer a cyberattack go out of business within six months, according to CrowdStrike’s research. Beyond the financial damage, cyberattacks can destroy customer trust, lead to regulatory penalties, and result in litigation.
I’ve seen firsthand how a single security incident can undo years of business building. Cybersecurity isn’t just an IT issue—it’s a business survival issue.
Do small businesses need a designated information security expert?
While not always necessary to have an in-house expert, small businesses should either have dedicated IT staff with security training or partner with managed IT services providers. The key is having someone accountable for security who understands your business context.
In my experience, the most successful approach for most small businesses is a hybrid model: some internal expertise combined with specialized external support, as highlighted in BD Emerson’s analysis.
How can small businesses protect against data breaches?
Beyond the fundamentals we’ve covered, businesses should:
- Encrypt sensitive data both at rest and in transit
- Use Data Loss Prevention (DLP) tools to monitor for unusual data movements
- Classify all information to ensure appropriate protection levels
- Implement access controls based on the principle of least privilege
- Regularly audit who has access to what information
Remember that data protection isn’t just good security—it’s often legally required under regulations like GDPR, CCPA, and industry-specific regulations. Managed IT support services can help ensure compliance with these requirements.
What should a small business do in case of a cyberattack?
Having an Incident Response Plan (IRP) is crucial. This plan should outline steps for:
- Identifying the breach scope and containing the damage
- Eradicating the threat
- Recovering affected systems through your disaster recovery procedures
- Notifying affected parties as required by law
- Conducting a post-incident review to prevent similar breaches
“The difference between a data breach being a bump in the road versus a business-ending event often comes down to how prepared you were to respond,” notes a cybersecurity expert at Compass MSP.
Is it safe for employees to use their own devices for work?
BYOD (Bring Your Own Device) can be safe if there’s a proper policy in place that includes:
- Mobile Device Management (MDM) solutions
- Clear separation between personal and business data
- Remote wiping capabilities for lost or stolen devices
- Encryption requirements
- Approved application lists
The key is balancing employee convenience with security requirements. In 2025, secure BYOD isn’t just possible—it’s a competitive advantage for recruiting and retaining talent, according to FTC guidance.
How can small businesses overcome limited resources and expertise in cybersecurity?
Small businesses can leverage:
- AI-powered cybersecurity solutions that reduce the need for human monitoring
- Security-as-a-Service offerings that provide enterprise-grade protection on a subscription basis
- Cloud-based security tools that don’t require on-premises infrastructure
- Cybersecurity frameworks designed specifically for small businesses
- Government resources like those provided by CISA and the SBA
- Managed IT services NYC providers who specialize in small business security
“The democratization of advanced security technologies has been a game-changer for small businesses,” according to security researchers at StrongDM.
Conclusion
Cybersecurity for small businesses isn’t just about preventing attacks—it’s about ensuring business continuity, protecting your reputation, and maintaining customer trust. In 2025, cybersecurity has become a fundamental business function, as essential as accounting or sales.
I’ve seen too many small business owners postpone security investments because they seemed complex or costly, only to face devastating consequences later. Don’t let your business become another statistic.
Start by implementing these ten practices, beginning with the ones most relevant to your specific risks. Consider partnering with a reputable managed IT services provider who can help you navigate the complex cybersecurity landscape. Remember that cybersecurity is a journey, not a destination—it requires ongoing attention and adaptation as threats evolve.
What cybersecurity measure will you implement first? Has your business faced security challenges? I’d love to hear your experiences and answer your questions in the comments below.
FAQ: Cybersecurity Best Practices for Small Businesses
What are the most critical cybersecurity measures small businesses should prioritize in 2025?
Small businesses should prioritize strong password policies and management, multi-factor authentication (MFA) on all accounts, keeping all software and systems updated, and providing ongoing security awareness training to employees. Implementing these foundational practices significantly reduces the risk of falling victim to common cyberattacks like phishing and malware. Additionally, backing up data regularly and testing the restoration process is crucial to protect against data loss from ransomware or other incidents.
Why are small businesses such frequent targets of cyberattacks?
Small businesses are often targeted because they are seen as “low-hanging fruit” by cybercriminals. They often lack the robust security infrastructure and expertise of larger enterprises, making them easier to compromise. Attackers recognize that small businesses possess valuable data, and may have connections to larger organizations, making them a potential entry point for supply chain attacks.
How can small businesses with limited IT resources effectively implement cybersecurity measures?
Small businesses can overcome resource constraints by partnering with Managed Security Service Providers (MSSPs) to provide 24/7 security monitoring, threat detection, and compliance assistance. Leveraging cloud-based security solutions and AI-powered cybersecurity tools can also automate security tasks and reduce the need for extensive in-house expertise. Additionally, businesses can explore cybersecurity frameworks specifically designed for small businesses, and take advantage of government resources offered by agencies like CISA and the SBA.
What is a “zero-trust” security model, and how can it benefit a small business?
A zero-trust security model operates on the principle of “never trust, always verify.” Instead of assuming that everything inside a network is safe, it requires every user, device, and application to be authenticated and authorized before being granted access. This means verifying every access request is authenticated, authorized, and encrypted; access is granted on a “least privilege” basis; and continuous monitoring and verification of users. Small businesses can benefit from improved security posture and reduced risk of breaches by reducing the attack surface and limiting the impact of compromised accounts or devices.
What are the key components of an effective incident response plan (IRP), and why is it important to test it regularly?
An effective IRP includes clearly defined roles and responsibilities, step-by-step procedures for handling different types of incidents, communication templates for stakeholders, documentation requirements for compliance, and recovery procedures. Regular testing through tabletop exercises helps identify gaps in the plan before a real incident occurs, ensuring that the business can respond quickly and effectively to minimize damage and downtime. Businesses that tested incident response plans recover from cyberattacks faster and with lower costs.
How does cloud security differ from traditional on-premises security, and what steps should small businesses take to secure their cloud services?
In the cloud, the responsibility for security is shared between the cloud provider and the business. While the provider secures the underlying infrastructure, the business is responsible for securing its data and access. Small businesses should implement cloud access security brokers (CASBs) to monitor cloud activity, data loss prevention (DLP) tools to prevent data leakage, cloud-native security tools offered by providers, and regularly assess their cloud configurations to prevent misconfigurations that can lead to data breaches.
What are some of the services offered by Hudson Infosys, and how can they help small businesses?
Hudson Infosys offers a comprehensive range of technology services, including managed IT support and preventative maintenance programs, to help businesses enhance operations, improve efficiencies, and increase business value. Their services are tailored to meet the specific needs of businesses of all sizes. They assist small businesses in making informed technology decisions, provide expert support to address IT challenges, and ensure operations run smoothly.
What are the biggest cybersecurity threats for small businesses, and how has that threat landscape changed in recent years?
In 2025, ransomware attacks, social engineering (especially phishing), and data breaches continue to be major threats. The increasing reliance on cloud services introduces new risks of misconfiguration and data leakage. Supply chain attacks, where hackers target smaller vendors to access larger companies, have also increased significantly. The growing sophistication of attacks means that traditional security measures are often insufficient, necessitating the adoption of advanced solutions like endpoint protection platforms and zero-trust architectures.