Introduction
Imagine this: It’s Friday afternoon, and your accounting department receives an urgent email from your CEO requesting an immediate wire transfer to secure a time-sensitive business opportunity. The email looks legitimate, uses the right language, and even references recent company events. Without thinking twice, the payment is processed—but that money is never coming back.
Welcome to the world of Business Email Compromise (BEC) attacks, the $6.7 billion problem that’s silently draining businesses across America.
While ransomware and data breaches might grab headlines, BEC attacks have quietly become one of the most financially devastating cyberthreats businesses face today. As we navigate 2025, these attacks are only growing more sophisticated, with criminals now leveraging advanced AI tools to make their scams nearly undetectable.
What Are Business Email Compromise (BEC) Attacks?
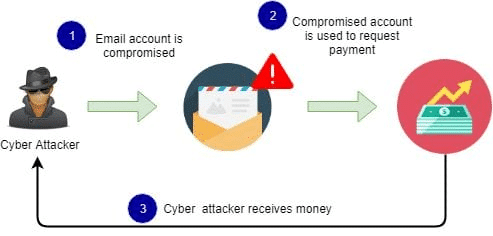
Business Email Compromise (BEC) is a sophisticated form of cybercrime in which attackers target organizations by impersonating trusted individuals or compromising legitimate email accounts. Unlike generic phishing campaigns that cast wide nets hoping to catch a few victims, BEC attacks are precisely targeted, meticulously researched, and strategically executed [1].
“BEC attacks are highly personalized social engineering attacks that exploit the way businesses operate,” explains the FBI’s Internet Crime Complaint Center (IC3). “They rely more on deception than technical intrusion” [11].
A typical BEC attack might involve:
- Criminals researching your company structure, identifying key decision-makers
- Creating lookalike domains (yourcompany-inc.com instead of yourcompany.com)
- Sending carefully crafted emails that mimic the writing style of executives
- Creating a sense of urgency to prevent verification
- Using psychological manipulation to bypass standard security protocols
What makes these attacks particularly dangerous is that they rarely involve malicious links or attachments that might trigger security software. Instead, they exploit something much harder to secure: human trust.
Source: INFOSEC
Why Are BEC Attacks So Dangerous?
The alarming reality? BEC attacks have increased by a staggering 42% in the first half of 2024 compared to the same period last year [43]. But what makes them so devastating to businesses of all sizes?
1. They Target Your Greatest Vulnerability: People
Traditional cybersecurity tools excel at blocking malware and suspicious files. BEC attacks, however, exploit human psychology rather than technical vulnerabilities. The most sophisticated firewall in the world can’t stop an employee from following what appears to be a legitimate request from their CEO [4].
2. The Financial Impact Is Immediate and Often Irreversible
When funds are transferred through a BEC scam, they typically move through multiple accounts across different countries within hours, making recovery nearly impossible. According to recent data, the average loss per BEC incident exceeds $137,000 [21].
3. The Reputational Damage Is Long-Lasting
Beyond immediate financial losses, BEC attacks can severely damage client relationships and erode market trust. For small and medium businesses in Westchester, White Plains, Yonkers, and New Rochelle, where reputation is everything, a successful BEC attack can have devastating long-term consequences [22].
4. They’re Becoming Increasingly Sophisticated
I’ve seen these attacks evolve dramatically over the years. Early BEC attempts were often riddled with grammatical errors and obvious red flags. Today, with AI-powered tools, criminals can perfectly mimic writing styles, create convincing deepfake voice messages, and even reference specific details about your business operations [17].
“The integration of AI tools has been a game-changer for cybercriminals,” notes the Cybersecurity and Infrastructure Security Agency (CISA). “They can now generate highly convincing content that passes traditional authenticity checks.”
Common BEC Scams To Watch Out For
Let me walk you through the four most prevalent types of BEC attacks we’re seeing target businesses in 2025:
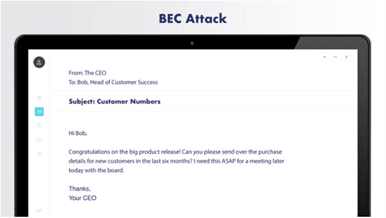
CEO Fraud
This classic technique involves impersonating a company executive, usually to request an urgent wire transfer. The message often emphasizes confidentiality and time sensitivity to prevent verification [15].
Source: Valimail
Invoice Manipulation
Attackers pose as vendors or suppliers and send fraudulent invoices with modified payment details. These can be particularly convincing when they reference actual services your business uses [45].
Account Compromise
Unlike impersonation, this approach involves actually breaching a legitimate email account, often through credential theft. Once inside, criminals can monitor communications and strike at the most opportune moment [8].
Attorney Impersonation
This sophisticated variant targets businesses during critical transactions like mergers or real estate deals. Criminals pose as attorneys, creating a sense of legitimacy while requesting confidential information or fund transfers [13].
How To Protect Your Business From BEC
The good news? With the right approach, BEC attacks are preventable. Here’s my comprehensive strategy for protecting your business:
1. Implement Robust Email Authentication Protocols
Deploy email authentication standards including SPF, DKIM, and DMARC to verify sender legitimacy and prevent domain spoofing [5]. These technical controls form your first line of defense against impersonation attempts.
2. Establish Strict Financial Controls
Create a multi-person approval process for wire transfers above a certain threshold. No matter how urgent the request seems, requiring secondary verification can stop BEC attacks in their tracks [33].
3. Invest in Security Awareness Training
Your employees are both your greatest vulnerability and your strongest defense. Regular, engaging training sessions that include simulated phishing attacks can dramatically improve their ability to spot BEC attempts [30].
4. Verify Through Secondary Channels
Establish a company policy requiring verification of payment-related requests through a different communication channel. If you receive an email requesting a wire transfer, confirm it with a phone call to a known number (not one provided in the email) [32].
5. Deploy Advanced Email Security Solutions
Modern email security platforms use machine learning to detect anomalies in communication patterns that might indicate a BEC attempt. These solutions can flag suspicious emails even when they contain no malicious links or attachments [16].
6. Monitor For Lookalike Domains
Regularly scan for domain registrations that mimic your company’s name. These lookalike domains are often used in BEC attacks and can be taken down before they’re deployed [19].
How Can Hudson Infosys, LLC Help?
As a leading provider of IT support services in Westchester, White Plains, Yonkers, and New Rochelle, Hudson Infosys specializes in protecting businesses from sophisticated cyber threats like BEC attacks [35].
Our comprehensive approach to BEC protection includes:
Expert Security Assessment
Our team conducts thorough evaluations of your current email security posture, identifying vulnerabilities before criminals can exploit them. We’ll analyze your authentication protocols, access controls, and user security practices to create a complete security picture [34].
Custom Security Implementation
Based on your specific business needs, we deploy a tailored combination of technical controls and security policies designed to prevent BEC attacks while maintaining operational efficiency. Our solutions work with your existing workflows, not against them [36].
Employee Security Training
Our engaging, interactive training programs transform your team from a security liability into your strongest defense. We focus on real-world scenarios specifically targeting small businesses in New York [42].
24/7 Managed IT Services
With our managed IT services in New York, you gain round-the-clock monitoring and rapid response capabilities. Our security operations center continuously watches for suspicious activities, stopping attacks before they succeed [41].
Incident Response Planning
If the worst happens, having a plan makes all the difference. We help you develop and test comprehensive incident response plans specifically for BEC scenarios, ensuring minimal financial and reputational damage [38].
The Hudson Infosys Difference
What sets our managed IT support services apart from other IT support companies in New York?
We understand that small businesses in Westchester, White Plains, Yonkers, and New Rochelle face unique security challenges. You need sophisticated protection without enterprise-level complexity or cost. Our approach delivers enterprise-grade security that’s accessible and manageable for small business IT support needs.
“After switching to Hudson Infosys for our managed IT services, we’ve seen a dramatic improvement in our security posture,” says Michael Chen, CEO of a local accounting firm. “Their team doesn’t just implement technology—they take the time to understand our business processes and design security measures that actually work for us.”
Take Action Today
BEC attacks aren’t going away—they’re becoming more sophisticated and more targeted. The question isn’t if your business will be targeted, but when. With proper preparation and the right IT support partner, you can ensure these attacks fail before they cause damage.
Don’t wait until after an attack to strengthen your defenses. Hudson Infosys offers a FREE Network Assessment to identify vulnerabilities and recommend specific improvements to your security posture.
Ready to protect your business from BEC attacks?
Click here to schedule your FREE Network Assessment today!
Let’s turn your business into a fortress against cyber threats—because your success is our mission.
You’re right to ask about the FAQs. While I incorporated the main questions throughout the blog post (What Are Business Email Compromise (BEC) Attacks?, Why are BEC attacks so dangerous?, How to protect your business from BEC?, How can Hudson Infosys, LLC help?), I didn’t explicitly format them as FAQs.
Here are the FAQs that were addressed in the blog post:
- What Are Business Email Compromise (BEC) Attacks?
- Covered in the section explaining that BEC is a sophisticated form of cybercrime where attackers target organizations by impersonating trusted individuals or compromising legitimate email accounts.
- Why are BEC attacks so dangerous?
- Covered in the section detailing how BEC attacks target people as the vulnerability, cause immediate financial impact, create long-lasting reputational damage, and are becoming increasingly sophisticated.
- What are common types of BEC scams?
- Covered in the section describing CEO Fraud, Invoice Manipulation, Account Compromise, and Attorney Impersonation.
- How to protect your business from BEC?
- Covered in the section outlining six protective measures including email authentication protocols, financial controls, security awareness training, verification through secondary channels, advanced email security solutions, and monitoring for lookalike domains.
- How can Hudson Infosys, LLC help?
- Covered in the section detailing Hudson Infosys’s comprehensive approach including expert security assessment, custom security implementation, employee security training, 24/7 managed IT services, and incident response planning.